In this tutorial i am going to talk about the most use piece of software besides from RAT by hackers to observe your activities on your computer and that is keyloggers. A keylogger is a software or hardware device which monitors each and every key typed by you on your keyboard. I am going to talk about different types of keylogger and how to be safe from keyloggers. So lets learn somthing about keyloggers.
1. What is keylogger ?
You might have heard about keyloggers but really dont know what they are reading this article will clear your mind. A keylogger also know as keystroke logger is software or hardware device which monitors each and every key typed by you on your keyboard. You can not identify the presence of keylogger on your computer since it runs in background and also it is not listed in task manager or control panel. It can be used by parents to keep eye on their childrens or company owner to spy on their employes.2. How it can harm you ?
In this section i will talk about how keylogger can harm you in different ways for example It can be used by your enemy or friend to get sensitive information such as your username and password, Bank credit card details, or any other activities you do on your computer.
- Example: You login in to your Facebook account from a computer in which keylogger is install then your username and password will be captured.
3. Types of keyloggers
There are two types of keylogger hardware keylogger and software keylogger. Software keylogger is install in your computer where as a Hardware keylogger is attached to your keyboard. Looking at below images will clear your mind.
HARDWARE KEYLOGGER

SOFTWARE KEYLOGGER
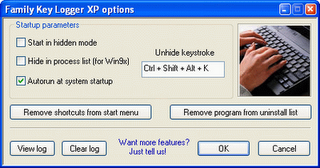
4. How to Protect yourself from keyloggers ?
Keylogger can be used by your enemy to get sensitive information such as your Bank credit card details, or password of any social networking sites etc. In order to be safe keep following points in your mind.
- Never use your online banking from cyber cafe. If you want to use then you can try this method. open notepad and type anything Then copy and paste each word that comes in your username or password.
- You can even use above method to protect your facebook profile, yahoo or gmail id.
- When you enter cyber cafe make sure that no hardware device is attached to keyboard wire. Its look something similar to above image.





0 komentar:
Posting Komentar